What are Security Roles
Following some great topics within ALM and deployments, your governance frameworks need to be enabled securely. This means adopting various security methods to your framework. Methods such as DLP Policies, Security Roles and more need to be factored in. For now, let us touch on Security Roles.
Power Platform Security Roles are a set of complex level associated permissions that determine available actions, access and rights users have within Power Platform environments and solutions. Security Roles dive deeper than just granting users access to solutions. They are used to control process driven data access within the platform ensuring only appropriate access is granted to necessary users when and where required.
Security Role Privileges
Built-in Security Roles
There are tons of existing Security Roles already in Power Platform, and Admins also maintain the rights to create new roles as well as customize existing roles. Diving into all the existing roles will be somewhat lengthy, but the below Security Roles, in my opinion, are the most commonly used and are ideal to gain clarity on:
- System Administrator: This is a role you need to carefully consider. These permissions grant users full control over all aspects of the Power Platform allowing them to perform all administrative tasks and functions. This includes being able to manage users and security roles, create and manage environments, and access all data and resources.
- Environment Maker: Users holding this Security Role can create and manage environments, but lack the rights and access to all administrative functions or data. Additionally, user assigned with this role can distribute their apps to other users within the organization.
- Basic User: The Basic User can create and play apps within shared environments and interact with records and data they own or with data that has been shared with them.
- Approval User: A commonly left our role that grants users the ability to interact with approvals. When you install the Approval solution in your environment, be sure to assign the role accordingly.
Custom Security Roles
Even with the amount of built-in roles, the Power Platform offers admins the ability to create custom security roles and also edit the built-in roles. Admins can create these custom roles with specific permissions and access levels based on data and organization requirements. This ensures that data and resources are secured and granted to appropriate users.
When creating new roles, admins can set privileges and access to various entity types and services based on a table level. Identifying all the privileges in each table is difficult to highlight, but the below screenshot can help visualize the level or security and privileges admins can apply per table:
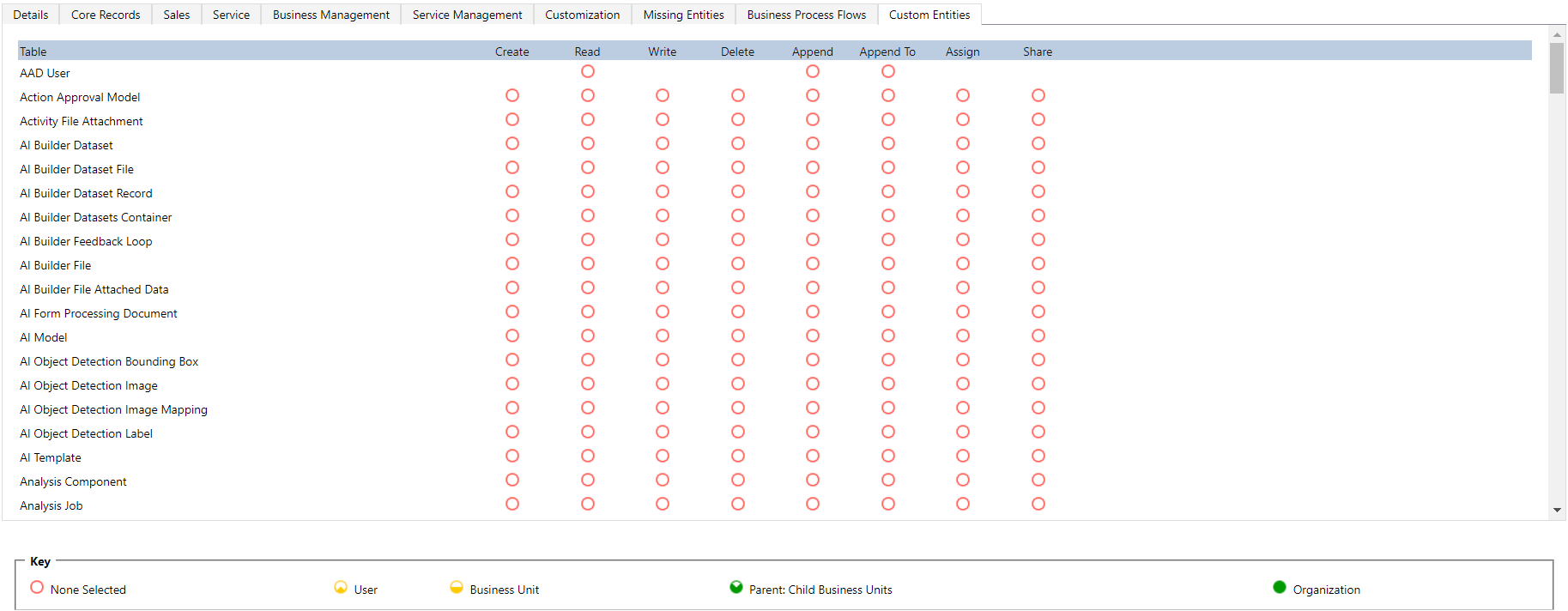
Security Roles can be managed at a Team or individual user level, sometime both. Within each role, there are various privilege types ranging from table data access to privacy and export control. Within various permissions, the following privileges can be applied to tables and its data:
Create, Read, Write, Delete, Append, Append To, Assign & Share.
Within each privilege, admins can also define the access level as to how the user can perform the privilege within the organization. These Access Levels include;
Organization, Parent: Child Business Unit, Business Unit, User & None.
Some tips for managing Security Roles
- Identify: Before creating new Security Roles, identify what you want to achieve with various roles and how you want to apply them. This could be to accommodate data access per department, or structure a parent hierarchy data model for managers and their teams.
- Principle of Least Privilege: This principle follows the concept of locking everything up as tight as possible, and applying access in small doses. This can be done at a job function level and reduces the risk of data breaches.
- Reuse: Streamline and reuse your Security Roles so you don’t land up with replicas or unnecessary roles.
- Document: A great way to manage lots of different active Security Roles is to document what the role is, what access and privileges are granted with it, appropriate roles that it should be assigned to, and users that currently hold that role.
- Review: Keep tabs on your Security Roles and re-evaluate the purpose, needs and assignments of them on a scheduled basis.
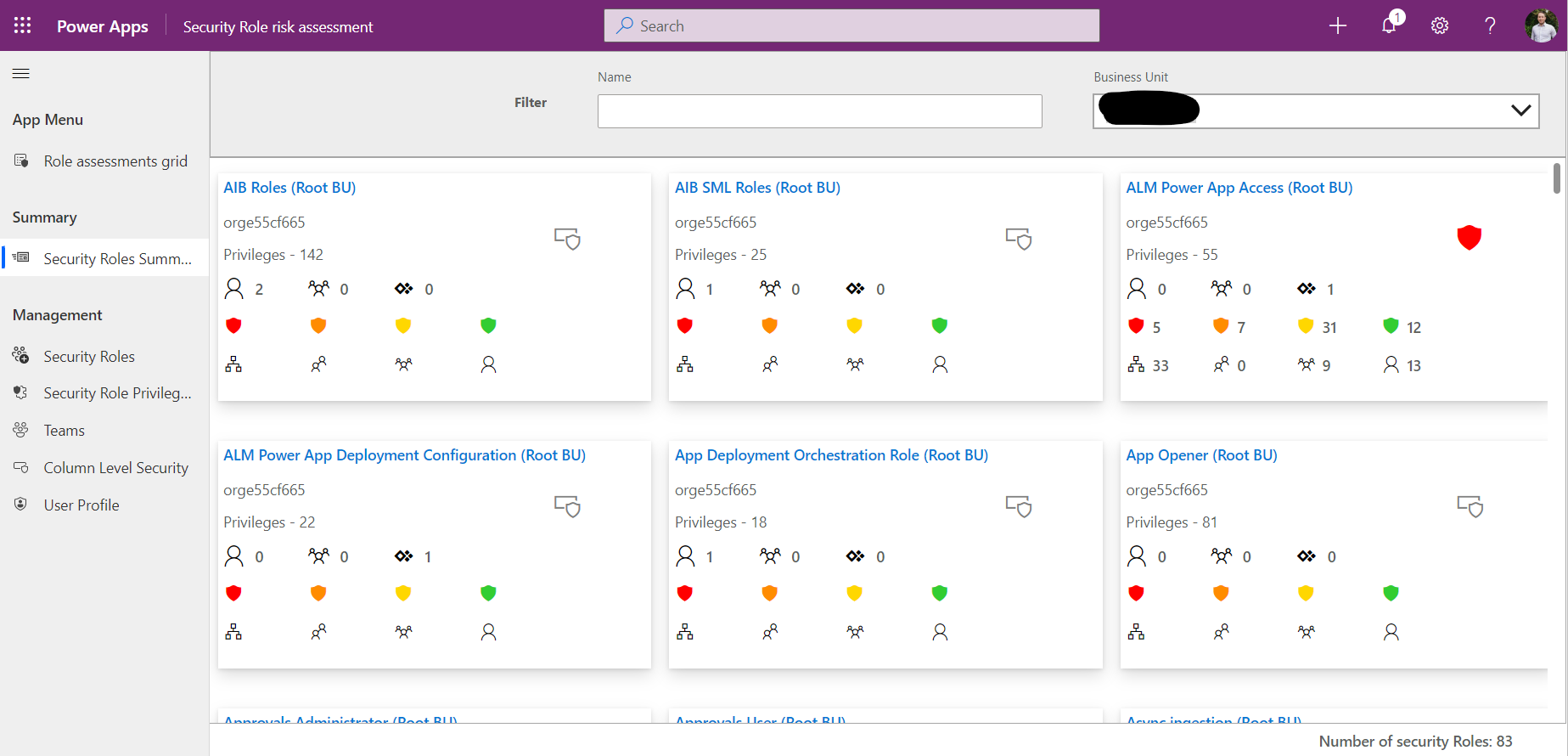
Security Risk Assessment and Management
A fantastic tool that you can import into your Power Platform environments, is the Security Risk Assessment and Management solution. This solution allows you to view all available Security Roles with user assignments as well as run security risk assessments on all your roles to help identify possible breach risks within your organization.
After testing the solution in my developer environment, I found the solution incredibly insightful and efficient. Aside from the detailed risk assessment and visual results it offers, admins can also manage role assignment, privilege management and column security. It does require your to install the Creator Kit first, but following the below instructions, you’ll be up and running in now time:
Download here.